Quad9 dns servers
Author: f | 2025-04-24
In my case, I use the Quad9 DNS servers. Step 1: Ensure Quad9 DNS servers are used. Go to System General Settings and under DNS servers add IP addresses for Quad9 DNS servers and select the WAN gateway. Make sure the DNS Server Override is unchecked as we don’t want the Quad9 DNS servers being changed by the ISP. Step 2:
DoH with Quad9 DNS Servers
That users in various regions can experience better performance than traditional DNS services.We have tested with quad9 on benchmarking tools, and here are the results:Analysis conducted using DNS Benchmark software by Steve GibsonThe result shows that Quad9 is the winner in terms of quick response time and lowest latency. Cloudflare’s 1.1.1.1 and Open DNS provide good performance, too, but Quad9 remains unbeatable here. Google’s DNS came last in this test, surprisingly.According to dnsspeedtest.online:DNS Performance of Quad9 (miliseconds)MinMedianAverage13.5013.8514.70Quad9 DNS delivered a response time of 14.70 milliseconds, which is good.We hit the following websites with Quad9 to get the raw performance:As you can see from the above results, Quad9 provides decent performance.CloudflareCloudflare’s 1.1.1.1 is a robust DNS server known for its speed, security, and reliability.According to our test, it delivers a 13.93-millisecond ping on average, which is good for online gaming and streaming. Additionally, it comes with built-in DDoS protection and supports DNSSEC to prevent attacks such as DNS spoofing and cache poisoning.Have a look at the below table:DNS Performance of Cloudflare (milliseconds)MinMedianAverage15.9017.8513.93We hit the following websites with Cloudflare to get the raw performance:According to the test, Cloudflare’s 1.1.1.1 provides decent performance.Google DNSGoogle Public DNS is the most common DNS server widely used by businesses and individuals. It’s also known for its faster response times, leveraging a vast network of global data centers to provide quick responses from anywhere in the world.Although Google DNS is a good and easy DNS solution, it is not the best. Refer to the below table for its ping response in milliseconds.DNS Performance of Google DNS (milliseconds)MinMedianAverage44.0047.9547.54We hit the following websites with Google Public DNS to get the raw performance:Based on the test, Google DNS provides quite good performance overall.NextDNSNextDNS is a versatile and privacy-focused DNS service that enhances online security and browsing experience through customization options. It’s a cloud-based DNS resolver that manages DNS queries securely and efficiently. NextDNS uses a global network of servers to reduce response times and ensure DNS queries are answered quickly. This helps gamers connect to game servers faster, giving them a competitive advantage when playing FPS games.On average, it delivers 49.64 milliseconds of ping time, which is quite good for gaming.DNS Performance of FlashStart DNS (milliseconds)MinMedianAverage45.0049.8049.64We hit the following websites with NextDNS to get the raw performance:It delivered stable results throughout the test, and we could customize the DNS according to our requirements. It’s quite easy to set up and has a user-friendly web panel for better accessibility and control over DNS usage. OpenDNSOpenDNS, developed by Cisco, is a well-known DNS service provider known primarily for its security, reliability, and speed. It delivers a stable internet connection and faster load times for an optimal gaming experience without lag spikes.Additionally, it’s well known for its security measures and privacy protection against cyber threats. It is ideal for gamers who want to protect their online streams from DDoS attacks and other potential attacks while gaming. Refer to the below table:DNS Performance of OpenDNS (milliseconds)MinMedianAverage60.3062.7062.54We hit the following websites with OpenDNS to get
Changing DNS Server to Quad9
This topic has been deleted. Only users with topic management privileges can see it. Ok so I have been using Pfsense for a bit now and am adding things one by one. So right now I am trying to get quad9 setup with DNS resolver. I came across this article but not sure how accurate it is because I have come across similiar articles with somewhat different settings.So current settings:System --> General SetupDNS Servers: 9.9.9.9 and 149.112.112.112DNS Server Override: uncheckedDisable DNS Forwarder: uncheckedServices --> DNS Resolver --> General SettingsEnable DNS Resolver: CheckedNext few items defaultDNSSEC: CheckedPyhton Module: UncheckedDNS Query Forwarding: CheckedUse SSL/TLS: CheckedDHCP Registration: UncheckedStatic DHCP: uncheckedOpenVPN Clients: uncheckedIf I look at System information:DNS server(s)127.0.0.19.9.9.9149.112.112.112Why is 127.0.0.1 in that list?If I run this per that article - nslookup isitblocked.orgResults:Server: Name of boxAddress: IP address of my pfsense box*** Name of box can't find isitblocked.org: Server failedAlso if I go to Diagnostics -> DNS LookupI get the followingName server Query time127.0.0.1 30 msec9.9.9.9 7 msec149.112.112.112 2 msecAgain why 127.0.0.1 ?Any help would be great on if the above settings are correct?Then I can move onto some more testing to verify it is working correctly. Again why 127.0.0.1Do not use the forwarder.I hope this helps, br Krisz You even wrote this: Use SSL/TLS: CheckedDoes Quad9 support DNS over TLS? YESWe do support DNS over TLS on port 853 (the standard) using an auth name of dns.quad9.net.therefore, it is necessary to specify this field: dns.quad9.netLike: Of course, this is an example from myQuad9 DNS Servers in Global - DNS Checker
Show you the corresponding IP address.Also, you can use ping commands like ping As shown in the above picture, the domain is resolved as the DNS server responded. Alternatively, you can also use online tools to check your DNS performance.How to Flush DNS?You may need to flush your DNS to refresh the DNS servers after the change. For Windows (10 and 11)Click the Start button and type cmd in the search bar.Right-click on Command Prompt and select Run as administrator.Type the following command: ipconfig /flushdns and press enter. You should see a message verifying that the DNS Resolver Cache was flushed.For macOSPress Command + Space to open Spotlight, type Terminal, and hit Enter.Depending on your macOS version, enter one of the following commands:For macOS Big Sur (11) or later:sudo killall -HUP mDNSResponderFor macOS Mojave (10.14) and earlier:sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponderEnter your administrator password if prompted, then press Enter.For Linux devicesThe method to flush DNS varies by distribution:Ubuntu (using systemd): sudo systemd-resolve –flush-cachesOther distributions using nscd: sudo /etc/init.d/nscd restartFAQsCan You Use 1.1.1.1 and 8.8.8.8 Together?Yes, you can use both 1.1.1.1 and 8.8.8.8 together as primary and secondary DNS. The primary server (1.1.1.1) is queried first for DNS resolution. If it fails to respond or cannot resolve the query, the device will query the secondary server (8.8.8.8).What is the Best DNS for PS5 Fortnite?The best DNS servers for PS5 and Fortnite gaming include Cloudflare (1.1.1.1), Google Public DNS (8.8.8.8), and Quad9. However, DNS performance may vary depending on your geolocation, your local ISP, and the game you are playing.What is a Good Connection Speed for PS5?For a smooth, lag-free gaming experience on PS5, you need at least 50-100 Mbps of internet connection. Ensure you have an optical fiber connection for the highest speed and stability. Lastly, use a suitable DNS server for your location and game.. In my case, I use the Quad9 DNS servers. Step 1: Ensure Quad9 DNS servers are used. Go to System General Settings and under DNS servers add IP addresses for Quad9 DNS servers and select the WAN gateway. Make sure the DNS Server Override is unchecked as we don’t want the Quad9 DNS servers being changed by the ISP. Step 2: 5. Quad9 DNS. Quad9 DNS is another free and public DNS server that you can use to route your traffic away from your ISP-provided DNS servers. Like other DNS servers on this list, once configured, Quad9 routes your DNS queries through aQuad9 DNS Servers - Whats My DNS
System, you use your own 9.9.9.9 setting. :-) @DaddyGoOk that fixed that part. Makes sense too after reading on it more. Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings? @cburbs said in Quad9 and DNS Resolver:Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings?In your place, situation with this setting, I would only give pfSense to the DNS server, so that your DNS could not leak. ( with DHCP, but still only the pfSense box should be the server.Be careful with DHCP server + pfblockerng, create static entries for DHCPit’s an old story, so you can avoid the unbond of restarting multiple times @cburbs said in Quad9 and DNS Resolver:Static DHCP: uncheckedWhat I forgot: :-)if you decide to... and use DHCP on your network, check this as well: Static DHCP: to checked (this is in view of my previous remark) @DaddyGoSo DNS should be pointing to my pfsense box?When I go to dnsleaktest I Get the following -207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United StatesThe last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up? @cburbs said in Quad9 and DNS Resolver:@DaddyGoSo DNS should be pointingDoH with Quad9 DNS Servers
To my pfsense box?When I go to dnsleaktest I Get the following -207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United StatesThe last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up?You will never see pure 9.9.9.9 DNS resolution, quad9 doesn't have its own network, therefore using CDN, as you can see WoodyNet, so I don't use it for 9.9.9.9 never, hmmmmm ( So it does seem to be working on that part then.Do you also use this in your setup? @cburbs said in Quad9 and DNS Resolver:So it does seem to be working on that part then.Do you also use this in your setup?There can be many approaches to this theme:Use what I have already described above for 853 DNSoverTLS + DNSSEC ( and then you can also block port 53 on the firewall as a rule.Don't forget the firewall is blocking all unsolicited traffic by default, this is the rule on pfSense.Another solution is to use Suricata and/or Snort with ET DNS rules, for example Addition: the pfSense is blocked from the WAN side, so if you think about the LAN side you can disable the external DNS query for the clients or as I mentioned ET DNS rules set will be the solution (IPS on LAN) @cburbs said in Quad9 and DNSChanging DNS Server to Quad9
DNS Changer: Fast & Secure DNS on PCDNS Changer: Fast & Secure DNS, coming from the developer Star Internet Services, is running on Android systerm in the past.Now, You can play DNS Changer: Fast & Secure DNS on PC with GameLoop smoothly.Download it in the GameLoop library or search results. No more eyeing the battery or frustrating calls at the wrong time any more.Just enjoy DNS Changer: Fast & Secure DNS PC on the large screen for free!DNS Changer: Fast & Secure DNS IntroductionSecure DNS improves internet speeds by modifying the default ISP DNS to your choice of Public DNS resolvers or DNSFLEX Secure DNS. Use DNS Changer to select from a list of top rated public DNS providers including Google, Cloudflare, Quad9, Verisign and more.Add an additional layer of online security with DOH (DNS over HTTPS). DOH works by encrypting DNS queries between your UE device and the DNS server, protecting your data from third party networks such as public WiFi hotspots or ISPs. Our servers are geo-located and distributed globally delivering low latency performance for sensitive gaming applications. Use our Speed Test utility to choose the closest public DNS server based on RTT latency.Get exclusive access to DNSFLEX Secure DNS services by downloading our DNS Changer App. Choose from two levels of additional security for free: Parental Control or Malware and Virus protection.Parental Control:* Blocks categories such as Adult, Guns/Violence, Ad-trackers and more * Enables safe search feature for search engines - Google, Bing, Yahoo and DuckDuckGo* Safe and supervised internet access for children Malware and Virus Protection:* Protects against malware and phishing attacks* Blocks DNS rebinding and ransomware attacks* Up to date threat intelligence feeds Main Features:* Supports Mobile Data (2G/3G/4G/5G) and WiFi networks * No root required* Low resource utilization (CPU/RAM)* Speed test tool to select the fastest DNS server* Supports Encrypted DOH (DNS over HTTPS) and UDP DNS* Add your own custom DNS server (UDP or DOH)* Select from a list of pre-configured public DNS servers* Select from a list of pre-configured public DOH servers* Access Geo blocked websites* Improves online gaming latency* Increases internetQuad9 DNS Servers in Global - DNS Checker
Quick Links Encrypted DNS Is More Private and Secure First, Choose a Supported Free DNS Service Next, Enable DNS over HTTPS in Windows 11 Summary Windows 11 allows you to encrypt your DNS requests through DNS over HTTPS (DoH), providing enhanced online privacy and security. To enable DoH on Windows 11, go to Settings > Network & Internet > Wi-Fi Properties > Hardware Properties and click the "Edit" button next to DNS Server. Enter a DNS server of your choice for IPv4 and IPv6, then make sure that "DNS Over HTTPs" is set to "On." For improved online privacy and security, Windows 11 lets you use DNS over HTTPS (DoH) to encrypt the DNS requests your computer makes while you browse or do anything else online. Here's how to set it up. Encrypted DNS Is More Private and Secure Every time you visit a website using a domain name (such as "google.com," for example), your computer sends a request to a Domain Name System (DNS) server. The DNS server takes the domain name and looks up the matching IP address from a list. It sends the IP address back to your computer, which your computer then uses to connect to the site. This domain name fetching process traditionally happened unencrypted on the network. Any point in between could intercept the domain names of the sites you are visiting. With DNS over HTTPS, also known as DoH, the communications between your computer and a DoH-enabled DNS server are encrypted. No one can intercept your DNS requests to snoop on the addresses you're visiting or tamper with the responses from the DNS server. First, Choose a Supported Free DNS Service As of Windows 11's release, DNS over HTTPS in Windows 11 only works with a certain hard-coded list of free DNS services (you can see the list yourself by running netsh dns show encryption in a Terminal window). Here's the current list of supported IPv4 DNS service addresses as of November 2023: Google DNS Primary: 8.8.8.8 Google DNS Secondary: 8.8.4.4 Cloudflare DNS Primary: 1.1.1.1 Cloudflare DNS Secondary: 1.0.0.1 Quad9 DNS Primary: 9.9.9.9 Quad9 DNS Secondary: 149.112.112.112 For IPv6, here is the list of supported DNS service addresses: Google DNS Primary: 2001:4860:4860::8888 Google DNS Secondary: 2001:4860:4860::8844 Cloudflare DNS Primary: 2606:4700:4700::1111 Cloudflare DNS Secondary: 2606:4700:4700::1001 Quad9 DNS Primary: 2620:fe::fe Quad9 DNS Secondary: 2620:fe::fe:9 When it comes time to enable DoH in the section below,. In my case, I use the Quad9 DNS servers. Step 1: Ensure Quad9 DNS servers are used. Go to System General Settings and under DNS servers add IP addresses for Quad9 DNS servers and select the WAN gateway. Make sure the DNS Server Override is unchecked as we don’t want the Quad9 DNS servers being changed by the ISP. Step 2: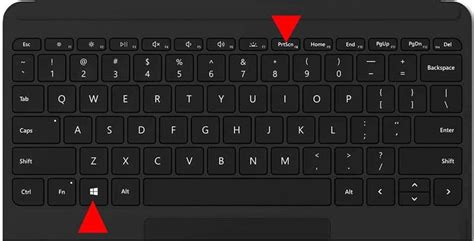
Quad9 DNS Servers - Whats My DNS
There a service that Quad9 offers that does not have the blocklist or other security?The primary IP address for Quad9 is 9.9.9.9, which includes the blocklist, DNSSEC validation, and other security features. However, there are alternate IP addresses that the service operates which do not have these security features. These might be useful for testing validation, or to determine if there are false positives in the Quad9 system.Secure IP: 9.9.9.9 Provides: Security blocklist, DNSSEC, No EDNS Client-Subnet sent. If your DNS software requires a Secondary IP address, please use the secure secondary address of 149.112.112.112Unsecure IP: 9.9.9.10 Provides: No security blocklist, DNSSEC, sends EDNS Client-Subnet. If your DNS software requires a Secondary IP address, please use the unsecure secondary address of 149.112.112.10Note: Use only one of these sets of addresses – secure or unsecure. Mixing secure and unsecure IP addresses in your configuration may lead to your system being exposed without the security enhancements, or your privacy data may not be fully protected--------------------------IPV6: there IPv6 support for Quad9?Yes. Quad9 operates identical services on a set of IPv6 addresses, which are on the same infrastructure as the 9.9.9.9 systems.Secure IPv6: 2620:fe::fe Blocklist, DNSSEC, No EDNS Client-SubnetUnsecure IPv6: 2620:fe::10 No blocklist, DNSSEC, send EDNS Client-SubnetDoH with Quad9 DNS Servers
Starting point. Lock things down better. @cburbs said in Quad9 and DNS Resolver:Also Do you have any rules under firewal/rules/wan?Yeeeepppp is actually the box for that.to your previous question: Also Do you have any rules under firewal/rules/wan?I don't like to load the WAN side with rules, it's like drilling a hole in a sieve, pfSense block all unsolicited traffic on the WAN, so I have more floating rules @DaddyGoI have a WAN rule called - Easy Rule: Passed from Firewall log view - says it was created by Easy Rule .Trying to figure out what it is -Protocol: IPv4 TCPSource: ISP IP addresDestination: 104.25.242.31Port: 80(HTTP)Destination IP is Carrier: cloudflareConfused? @cburbs said in Quad9 and DNS Resolver:Easy RuleYes it is, :-).did you add it this? with this? ( It has a date from almost a year ago. Could have as I think that is when I was looking at snort but was having all sorts of issues so I disabled it all.So I probably don't need that rule - I won't do anything with it now but remove it later today. Do you use squidguard on your system? That was the next thing I was going to implement. @cburbs said in Quad9 and DNS Resolver:squidguardI use HA proxy I think for my purposes more appropriate, Squid is problematic among MITM, so SquidGuard doesn't work for me eitherBut I strongly recommend installing Suricata/Snort and pfblockerNG-devel Delete the rule for said http 80 port because it is unnecessary!I didn’t investigate all the way. In my case, I use the Quad9 DNS servers. Step 1: Ensure Quad9 DNS servers are used. Go to System General Settings and under DNS servers add IP addresses for Quad9 DNS servers and select the WAN gateway. Make sure the DNS Server Override is unchecked as we don’t want the Quad9 DNS servers being changed by the ISP. Step 2:Changing DNS Server to Quad9
Here are 28 public repositories matching this topic... Code Issues Pull requests High performance DNS over HTTPS client & server Updated Feb 20, 2025 Go Code Issues Pull requests 纯净抗污染,简单轻量级 Updated Oct 9, 2024 C# Code Issues Pull requests Discussions Docker DNS server on steroids to access DNS-over-TLS from Cloudflare, Google, Quad9, Quadrant or CleanBrowsing Updated Nov 5, 2024 Go Code Issues Pull requests A DNS-protocol proxy for DNS-over-HTTPS providers, such as Google and Cloudflare Updated Sep 25, 2021 Go Code Issues Pull requests Google Kubernetes Engine GKE with DevOps 75 Real-World Demos Updated Aug 14, 2024 HTML Code Issues Pull requests A DNS abstraction for PHP Updated Feb 1, 2024 PHP Code Issues Pull requests Simple DNS over HTTPS Server Updated Dec 29, 2024 C# Code Issues Pull requests Different DNS servers for Magisk Updated Oct 2, 2024 Shell Code Issues Pull requests Tools to work with the Google DNS over HTTPS API in R Updated May 15, 2020 R Code Issues Pull requests HTTPDNS 库 Swift 实现(支持 DNSPod 与 AliyunDNS ) Updated Mar 6, 2018 Swift Code Issues Pull requests DNS-over-HTTPS proxy & client written in PHP to send DoH, DNSCrypt and GoogleDns queries Updated Sep 2, 2020 PHP Code Issues Pull requests A dynamic DDNS client for Google Cloud DNS Updated Oct 22, 2024 Python Code Issues Pull requests GoLang Google Domains Dynamic DNS API Update Client Updated Oct 2, 2020 Go Code Issues Pull requests Google public DNS lib for rust. Updated Nov 13, 2021 Rust Code Issues Pull requests A WordPress php library for interacting with the Google Public DNS API. Updated Aug 31, 2017 PHP Code Issues Pull requests A cross-platform python app to set and unset primary and secondary DNS Updated Dec 7, 2024 Python Code Issues Pull requests DNS over HTTPS universalComments
That users in various regions can experience better performance than traditional DNS services.We have tested with quad9 on benchmarking tools, and here are the results:Analysis conducted using DNS Benchmark software by Steve GibsonThe result shows that Quad9 is the winner in terms of quick response time and lowest latency. Cloudflare’s 1.1.1.1 and Open DNS provide good performance, too, but Quad9 remains unbeatable here. Google’s DNS came last in this test, surprisingly.According to dnsspeedtest.online:DNS Performance of Quad9 (miliseconds)MinMedianAverage13.5013.8514.70Quad9 DNS delivered a response time of 14.70 milliseconds, which is good.We hit the following websites with Quad9 to get the raw performance:As you can see from the above results, Quad9 provides decent performance.CloudflareCloudflare’s 1.1.1.1 is a robust DNS server known for its speed, security, and reliability.According to our test, it delivers a 13.93-millisecond ping on average, which is good for online gaming and streaming. Additionally, it comes with built-in DDoS protection and supports DNSSEC to prevent attacks such as DNS spoofing and cache poisoning.Have a look at the below table:DNS Performance of Cloudflare (milliseconds)MinMedianAverage15.9017.8513.93We hit the following websites with Cloudflare to get the raw performance:According to the test, Cloudflare’s 1.1.1.1 provides decent performance.Google DNSGoogle Public DNS is the most common DNS server widely used by businesses and individuals. It’s also known for its faster response times, leveraging a vast network of global data centers to provide quick responses from anywhere in the world.Although Google DNS is a good and easy DNS solution, it is not the best. Refer to the below table for its ping response in milliseconds.DNS Performance of Google DNS (milliseconds)MinMedianAverage44.0047.9547.54We hit the following websites with Google Public DNS to get the raw performance:Based on the test, Google DNS provides quite good performance overall.NextDNSNextDNS is a versatile and privacy-focused DNS service that enhances online security and browsing experience through customization options. It’s a cloud-based DNS resolver that manages DNS queries securely and efficiently. NextDNS uses a global network of servers to reduce response times and ensure DNS queries are answered quickly. This helps gamers connect to game servers faster, giving them a competitive advantage when playing FPS games.On average, it delivers 49.64 milliseconds of ping time, which is quite good for gaming.DNS Performance of FlashStart DNS (milliseconds)MinMedianAverage45.0049.8049.64We hit the following websites with NextDNS to get the raw performance:It delivered stable results throughout the test, and we could customize the DNS according to our requirements. It’s quite easy to set up and has a user-friendly web panel for better accessibility and control over DNS usage. OpenDNSOpenDNS, developed by Cisco, is a well-known DNS service provider known primarily for its security, reliability, and speed. It delivers a stable internet connection and faster load times for an optimal gaming experience without lag spikes.Additionally, it’s well known for its security measures and privacy protection against cyber threats. It is ideal for gamers who want to protect their online streams from DDoS attacks and other potential attacks while gaming. Refer to the below table:DNS Performance of OpenDNS (milliseconds)MinMedianAverage60.3062.7062.54We hit the following websites with OpenDNS to get
2025-04-03This topic has been deleted. Only users with topic management privileges can see it. Ok so I have been using Pfsense for a bit now and am adding things one by one. So right now I am trying to get quad9 setup with DNS resolver. I came across this article but not sure how accurate it is because I have come across similiar articles with somewhat different settings.So current settings:System --> General SetupDNS Servers: 9.9.9.9 and 149.112.112.112DNS Server Override: uncheckedDisable DNS Forwarder: uncheckedServices --> DNS Resolver --> General SettingsEnable DNS Resolver: CheckedNext few items defaultDNSSEC: CheckedPyhton Module: UncheckedDNS Query Forwarding: CheckedUse SSL/TLS: CheckedDHCP Registration: UncheckedStatic DHCP: uncheckedOpenVPN Clients: uncheckedIf I look at System information:DNS server(s)127.0.0.19.9.9.9149.112.112.112Why is 127.0.0.1 in that list?If I run this per that article - nslookup isitblocked.orgResults:Server: Name of boxAddress: IP address of my pfsense box*** Name of box can't find isitblocked.org: Server failedAlso if I go to Diagnostics -> DNS LookupI get the followingName server Query time127.0.0.1 30 msec9.9.9.9 7 msec149.112.112.112 2 msecAgain why 127.0.0.1 ?Any help would be great on if the above settings are correct?Then I can move onto some more testing to verify it is working correctly. Again why 127.0.0.1Do not use the forwarder.I hope this helps, br Krisz You even wrote this: Use SSL/TLS: CheckedDoes Quad9 support DNS over TLS? YESWe do support DNS over TLS on port 853 (the standard) using an auth name of dns.quad9.net.therefore, it is necessary to specify this field: dns.quad9.netLike: Of course, this is an example from my
2025-04-09System, you use your own 9.9.9.9 setting. :-) @DaddyGoOk that fixed that part. Makes sense too after reading on it more. Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings? @cburbs said in Quad9 and DNS Resolver:Also if I do an Ipconfig /all on my devices should it be using my pfsense box or the above DNS settings?In your place, situation with this setting, I would only give pfSense to the DNS server, so that your DNS could not leak. ( with DHCP, but still only the pfSense box should be the server.Be careful with DHCP server + pfblockerng, create static entries for DHCPit’s an old story, so you can avoid the unbond of restarting multiple times @cburbs said in Quad9 and DNS Resolver:Static DHCP: uncheckedWhat I forgot: :-)if you decide to... and use DHCP on your network, check this as well: Static DHCP: to checked (this is in view of my previous remark) @DaddyGoSo DNS should be pointing to my pfsense box?When I go to dnsleaktest I Get the following -207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United StatesThe last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up? @cburbs said in Quad9 and DNS Resolver:@DaddyGoSo DNS should be pointing
2025-04-10To my pfsense box?When I go to dnsleaktest I Get the following -207.162.219.52 None Lightpoint Colocation & Hosting LLC Beaverton, United States66.96.115.176 res100.pdx.rrdns.pch.net. WoodyNet United States66.96.115.177 res200.pdx.rrdns.pch.net. WoodyNet United States66.96.115.178 res300.pdx.rrdns.pch.net. WoodyNet United StatesThe last 3 I believe show quad9 is working correctly just not sure why I am getting the top IP which is a Colocation/Hosting place in my area? Why would this one show up?You will never see pure 9.9.9.9 DNS resolution, quad9 doesn't have its own network, therefore using CDN, as you can see WoodyNet, so I don't use it for 9.9.9.9 never, hmmmmm ( So it does seem to be working on that part then.Do you also use this in your setup? @cburbs said in Quad9 and DNS Resolver:So it does seem to be working on that part then.Do you also use this in your setup?There can be many approaches to this theme:Use what I have already described above for 853 DNSoverTLS + DNSSEC ( and then you can also block port 53 on the firewall as a rule.Don't forget the firewall is blocking all unsolicited traffic by default, this is the rule on pfSense.Another solution is to use Suricata and/or Snort with ET DNS rules, for example Addition: the pfSense is blocked from the WAN side, so if you think about the LAN side you can disable the external DNS query for the clients or as I mentioned ET DNS rules set will be the solution (IPS on LAN) @cburbs said in Quad9 and DNS
2025-04-23Quick Links Encrypted DNS Is More Private and Secure First, Choose a Supported Free DNS Service Next, Enable DNS over HTTPS in Windows 11 Summary Windows 11 allows you to encrypt your DNS requests through DNS over HTTPS (DoH), providing enhanced online privacy and security. To enable DoH on Windows 11, go to Settings > Network & Internet > Wi-Fi Properties > Hardware Properties and click the "Edit" button next to DNS Server. Enter a DNS server of your choice for IPv4 and IPv6, then make sure that "DNS Over HTTPs" is set to "On." For improved online privacy and security, Windows 11 lets you use DNS over HTTPS (DoH) to encrypt the DNS requests your computer makes while you browse or do anything else online. Here's how to set it up. Encrypted DNS Is More Private and Secure Every time you visit a website using a domain name (such as "google.com," for example), your computer sends a request to a Domain Name System (DNS) server. The DNS server takes the domain name and looks up the matching IP address from a list. It sends the IP address back to your computer, which your computer then uses to connect to the site. This domain name fetching process traditionally happened unencrypted on the network. Any point in between could intercept the domain names of the sites you are visiting. With DNS over HTTPS, also known as DoH, the communications between your computer and a DoH-enabled DNS server are encrypted. No one can intercept your DNS requests to snoop on the addresses you're visiting or tamper with the responses from the DNS server. First, Choose a Supported Free DNS Service As of Windows 11's release, DNS over HTTPS in Windows 11 only works with a certain hard-coded list of free DNS services (you can see the list yourself by running netsh dns show encryption in a Terminal window). Here's the current list of supported IPv4 DNS service addresses as of November 2023: Google DNS Primary: 8.8.8.8 Google DNS Secondary: 8.8.4.4 Cloudflare DNS Primary: 1.1.1.1 Cloudflare DNS Secondary: 1.0.0.1 Quad9 DNS Primary: 9.9.9.9 Quad9 DNS Secondary: 149.112.112.112 For IPv6, here is the list of supported DNS service addresses: Google DNS Primary: 2001:4860:4860::8888 Google DNS Secondary: 2001:4860:4860::8844 Cloudflare DNS Primary: 2606:4700:4700::1111 Cloudflare DNS Secondary: 2606:4700:4700::1001 Quad9 DNS Primary: 2620:fe::fe Quad9 DNS Secondary: 2620:fe::fe:9 When it comes time to enable DoH in the section below,
2025-04-13