Policy analyzer
Author: b | 2025-04-24

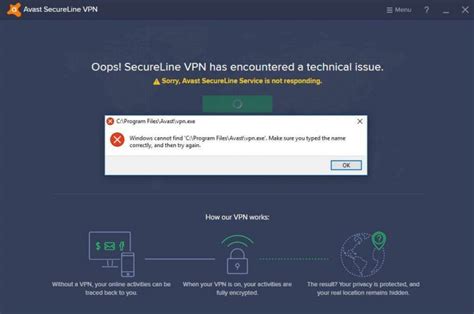
Can Policy Analyzer and Optimizer detect new changes to an already-analyzed policy and run analysis again on the same policy? No, the Policy Analyzer and Optimizer can analyze policies only when manually triggered or at a 24-hour scheduled policy analysis run.
Analyze Group Policy Objects with Microsoft Policy Analyzer
EN EnglishDeutschFrançaisEspañolPortuguêsItalianoRomânNederlandsLatinaDanskSvenskaNorskMagyarBahasa IndonesiaTürkçeSuomiLatvianLithuaniančeskýрусскийбългарскиالعربيةUnknown Login to YUMPU News Login to YUMPU Publishing CLOSE TRY ADFREE Discover products News Publishing Magazines Create ePaper Login to YUMPU News Login to YUMPU Publishing 13.07.2015 • Views Share Embed Flag Protocol Analyzer - EventHelix.com Protocol Analyzer - EventHelix.com SHOW MORE SHOW LESS ePAPER READ DOWNLOAD ePAPER TAGS protocol visualether analyzer template filter extraction sequence display destination examples eventhelix.com You also want an ePaper? Increase the reach of your titles YUMPU automatically turns print PDFs into web optimized ePapers that Google loves. START NOW More documents Recommendations Info Page 4: VISUALETHER PROTOCOL ANALYZER 6.1WiPage 9 and 10: VISUALETHER PROTOCOL ANALYZER 6.14 Page 11 and 12: VISUALETHER PROTOCOL ANALYZER 6.12 Page 13: VISUALETHER PROTOCOL ANALYZER 6.1BoPage 16 and 17: VISUALETHER PROTOCOL ANALYZER 6.1SpPage 18: VISUALETHER PROTOCOL ANALYZER 6.1DrPage 21 and 22: VISUALETHER PROTOCOL ANALYZER 6.1ExPage 23 and 24: VISUALETHER PROTOCOL ANALYZER 6.1ruPage 25 and 26: VISUALETHER PROTOCOL ANALYZER 6.1tcPage 27 and 28: VISUALETHER PROTOCOL ANALYZER 6.1SpPage 29 and 30: VISUALETHER PROTOCOL ANALYZER 6.1AtPage 31 and 32: VISUALETHER PROTOCOL ANALYZER 6.1WoPage 33 and 34: VISUALETHER PROTOCOL ANALYZER 6.1SIPage 35 and 36: VISUALETHER PROTOCOL ANALYZER 6.1LI Delete template? Are you sure you want to delete your template? Save as template ? Title Description no error products FREE adFREE WEBKiosk APPKiosk PROKiosk Resources Blog API Help & Support Status tuxbrain.comooomacros.orgnubuntu.org Company Contact us Careers Terms of service Privacy policy Cookie policy Cookie settings Imprint Terms of service Privacy policy Cookie policy Cookie settings Imprint Change language Made with love in Switzerland © 2025 Yumpu.com all rights reserved
Policy Analyzer - Analyzing and Comparing Group Policy Objects
Firewall Policy AnalyzerA no-risk, no-cost firewall analyzer to help enhance your security posture. One misconfigured rule is one too many Misconfigurations are a well-documented source of the expanding cybersecurity gap, especially when it comes to an organization’s firewall. With traditional rules-based firewall setups becoming cumbersome to manage manually as environments grow, human errors can quickly add up if not identified and corrected, compromising your entire security infrastructure.FireMon’s firewall Policy Analyzer simplifies the process of identifying and correcting misconfigurations, providing a fast, reliable solution to strengthen your security posture and close cybersecurity gaps. “99% of firewall breaches will be caused by misconfigurations, not firewalls.” Policy Analyzer that Reduces Risk FireMon Policy Analyzer is a complimentary firewall rule analysis solution that provides best practices and suggestions to reduce policy-related risk. Within minutes, our firewall analyzer shares a diagnostic report outlining the security hygiene of a single firewall configuration in your environment, complete with key areas of interest and remediation recommendations. Get a Demo FireMon Policy Analyzer Delivers: Assessment results available in minutes with no installation, setup, or dedicated hardware Key results include overly permissive, risky access, vendor hardening, and policy quality warnings Comprehensive analysis highlights gaps in compliance and security posture, enabling quick remediation and improved policy management Validation to see if changes improve diagnostic scores Downloadable reports to dive deeper into the results and share with others Top remediation recommendations based on FireMon’s 20+ years of experience Get a demo Protect Your Enterprise with Comprehensive Firewall Analyzer Tools Enhance security and compliance with advanced tools to monitor logs, analyze traffic in real time, and review policies—ensuring your firewall stays optimized and secure. Monitor and Analyze Firewall Logs Leverage a firewall log analyzer to gain visibility into network activity, detect threats, and ensure compliance. Track events, identify vulnerabilities, and strengthen security posture.ContinuouslyWhat is Policy Analysis? - Policy Analyze
It took us a little longer than we wanted but we are finally ready to announce new versions of LGPO and Policy Analyzer as well as two new tools, GPO2PolicyRules and SetObjectSecurity. These new and updated tools are now available on the Microsoft Download Center. The goal is to keep this post as short as possible so let’s just jump into the details.Two new options were added in LGPO.exe. The first, /ef which enables Group Policy extensions referenced in the backup.xml. The second, /p which allows for importing settings directly from a .PolicyRules file which negates the need to have the actual GPOs on hand. Additionally, LGPO.exe /b and /g now capture locally-configured client-side extensions (CSEs) (which we had an issue with previously). Lastly, /b also correctly captures all user rights assignments, overcoming a bug in the underlying “secedit.exe /export” that fails to capture user rights assignments that are granted to no one.The “Compare to Effective State” button has replaced the “Compare local registry” and “Local Policy” checkboxes that used to be in the Policy Analyzer main window. Press it to compare the selected baseline(s) to the current system state. If the selected baseline(s) contain any user configuration settings, they are compared against the current user’s settings. “Compare to Effective State” requires administrative rights if the selected baseline(s) include any security template settings or Advanced Auditing settings. The effective state corresponding to the selected baseline(s) settings are saved to a new policy rule set.Policy Analyzer now captures information about Group Policy Client-Side Extensions (CSEs) when you import GPO backups. From a Policy Viewer window, choose View \ Client Side Extensions (CSEs) to view the Machine and User CSEs for each baseline in the Viewer. (Note that LGPO.exe’s improved support for CSEs includes the ability to apply CSE configurations from Policy Analyzer’s .PolicyRules files.)Policy Analyzer now maps settings and sub-settings to display names more completely and more accurately, including mapping the GUIDs for Attack Surface Reduction (ASR) rules to their display names, and improved localization.You can now automate the conversion of GPO backups to Policy Analyzer .PolicyRules files and skip the. Can Policy Analyzer and Optimizer detect new changes to an already-analyzed policy and run analysis again on the same policy? No, the Policy Analyzer and Optimizer can analyze policies only when manually triggered or at a 24-hour scheduled policy analysis run.Policy analyzer - There's An AI For That
Digital assets. Why Are Up-to-Date Firewall Rules Important for Cybersecurity? Up-to-date firewall rules are crucial for cybersecurity because they ensure that only authorized traffic can access your network, effectively blocking malicious activity. As cyber threats evolve, outdated rules can leave vulnerabilities that attackers exploit.Regular updates and analysis of your firewall policies using a policy analyzer can help you adapt to new threats, maintain compliance, and optimize network performance. Without a system in place for analyzing rule sets, your network could become an easy target for cybercriminals, leading to potential data breaches and significant financial and reputational damage. What Benefits Does a Firewall Analyzer Offer? A firewall analyzer offers several benefits, including enhanced security through regular audits and compliance checks, ensuring firewall rules are optimized and up-to-date. It helps identify and rectify configuration errors, reducing the risk of breaches. Using an automated firewall policy analyzer will also provide visibility into network traffic, aiding in troubleshooting and performance optimization. Additionally, it simplifies management by generating reports and alerts, allowing administrators to proactively address potential issues and maintain robust security policies efficiently. Will a Policy Analyzer Reduce the Workload for My Security Team? Yes, a policy analyzer reduces your security team’s workload by automating rule analysis and identifying misconfigurations. Combined with firewall auditing software, it streamlines compliance checks, simplifies reporting, and provides remediation recommendations. This automation minimizes manual effort, enabling teams to focus on strategic initiatives while maintaining a secure and optimized firewall environment. What Types of Threats Are Commonly Detected with a Firewall Policy Analyzer? A firewall policy analyzer detects threats such as overly permissive rules, misconfigurations, unauthorized access attempts, and policy violations. It also identifies vulnerabilities from outdated rules, insecure protocols, and risky access paths. Combined with firewall auditing software, it helps uncover compliance gaps and weak points that attackers couldPolicy Analyzer - Analyzing and Comparing Group
If new rules need to be added. Policy Analyzer recommends how best to change your existing Security policy rules to meet your requirements without adding another rule, if possible.Streamline and optimize your existing rulebase—See where you can update your rules to minimize bloat and eliminate conflicts and also to ensure that traffic enforcement aligns with the intent of your Security policy rulebase. Test Security Rules (PAN-OS & Panorama) Test the traffic policy matches of the running firewall configuration. Panorama customers with the Cloud Connector Plugin can use Policy Analyzer to analyze Security rules both before and after committing changes to their configuration. Policy Analyzer not only analyzes and provides suggestions for possible consolidation or removal of specific rules to meet your intent but also checks for anomalies, such as Shadows, Redundancies, Generalizations, Correlations and Consolidations in your rulebase. Policy Analyzer requires the Cloud Connector Plugin 1.1.0 on your Panorama appliance.Policy Analyzer requires Panorama to be updated to PAN-OS version 10.2.3 or a later version. Both Panorama and PAN-OS customers can test and verify that security rules are allowing and denying the correct traffic by executing policy match tests for firewalls directly from the web interface. Select to perform a policy match or connectivity test. Enter the required information to perform the policy match test. In this example, we run a NAT policy match test.Select Test—Select NAT Policy Match.From—Select the zone traffic is originating from.To—Select the target zone of the traffic.Source—Enter the IP address from which traffic originated.Destination—Enter the IP addressPolicy Analyzer Command Line or any way to automate Policy Analyzer
Window, select the GPOs you want to compare, and click the “View / Compare” button. You’ll get a pop up with all the defined settings and what they are set to in each of the GPOs you are comparing. Gray cells indicate that setting isn’t configured in that policy, while yellow cells indicate values that conflict between the GPOs that are being compared. To find where each GPO option is configured, click the row in the table, and the Policy Path in the bottom detail window shows the path to the GPO option.Exporting to ExcelIf you have Excel installed on the computer you are running Policy Analyzer on, you can use the Export > “Export Table to Excel” feature to save the data to an Excel workbook. Since you probably don’t have Excel installed on your DCs, you can run Policy Analyzer locally on your workstation. To do so, copy the GPO backup folders to your computer after backing them up in the Group Policy Console on the server, and then import them into Policy Analyzer on your local PC. That will allow you to run the comparison and export the data to Excel for analysis. SummaryThis tool is helpful for in-depth analysis of Group Policy to help determine how GPOs in the domain differ from each other. You can use it for basic comparisons of GPOs, comparing custom compliance GPOs to a known-good baseline, or to help guide the consolidation of multiple GPOs. For more information about Policy Analyzer, see the official documentation.Policy Analyzer for allow policies - Google Cloud
Policy Analyzer is a tool released a couple of years ago that allows an administrator to easily compare two or more GPOs to find the differences between them. It’s a little clunky to use for quick troubleshooting, but for in-depth GPO work, this is a great tool for helping review and organize GPOs. Here, we’ll walk through how to get started and interpret the results. Get Set UpTo get started, download the Policy Analyzer tool from Microsoft at This download points to the Microsoft Security Compliance Toolkit, which Policy Analyzer is a part of. On the download page, you can opt to only download “PolicyAnalyzer.zip” which is the only file we need. Once that’s downloaded, copy it up to a server in the environment you are working on. It can either be a DC or a member server with the Group Policy console installed. From there, unzip the file and run PolicyAnalyzer.exe Preparing GPOsTo compare GPOs, we must first back them up to a folder on the local server. To do so:Open the Group Policy Management ConsoleExpand the OUs or Group Policy Objects container to find the GPOs you want to compareRight click the first GPO and select “Back up…”Enter a path to save the backup to. Ensure the folder you select doesn’t contain any other GPO backups, or the Policy Analyzer may have trouble importing them.Press the “Back Up” buttonRepeat steps 2-5 for each GPO you want to compare, ensuring you create a separate folder to store each GPO backup like in the structure below. Note that the GUID folder is created automatically by the backup, but the friendly folders (STIG 2012 R2 DC and Member Server) were created manually:Importing the GPOs to Policy AnalyzerBefore you can compare the GPOs, they must be imported into the Policy Analyzer tool. This process reads the GPO backup you created and creates a policy definition file that the tool can use.In Policy Analyzer, click the “Add…” buttonIn the popup, click File, then “Add Files from GPO(s)…”Browse to and select the folder where you saved the backupThe importer tool will show the different types of settings detectedClick the “Import…” buttonSave the policy rule definition file to the default folder, giving it a meaningful nameRepeat steps 1-7 for each GPO that you backed up previously Comparing the GPOsWith everything prepared, we can now actually compare 2 or more GPOs. In the main Policy Analyzer. Can Policy Analyzer and Optimizer detect new changes to an already-analyzed policy and run analysis again on the same policy? No, the Policy Analyzer and Optimizer can analyze policies only when manually triggered or at a 24-hour scheduled policy analysis run.
Security Policy mechatrolink-analyzer/mechatrolink-analyzer
Operates optimally, providing reliable protection against a variety of cyberthreats. Strata Cloud ManagerPAN-OS & Panorama Test Security Rules (Strata Cloud Manager) Test the traffic policy matches of your configuration. Updates to your Security rules are often time-sensitive and require you to act quickly. However, you want to ensure that any update you make to your Security policy rulebase meets your requirements and does not introduce errors or misconfigurations (such as changes that result in duplicate or conflicting rules). Policy Analyzer in Strata Cloud Manager enables you to optimize time and resources when implementing a change request. Policy Analyzer not only analyzes and provides suggestions for possible consolidation or removal of specific rules to meet your intent but also checks for anomalies, such as Shadows, Redundancies, Generalizations, Correlations and Consolidations in your rulebase. Use Policy Analyzer to analyze your Security rules both before and after you commit your changes. Pre-Change Policy Analysis—Enables you to evaluate the impact of a new rule so you can compare that to your intent for that rule and ensure that it does not duplicate or conflict with existing rules before you commit to avoid security rule inflation. You can also run a Security Policy Anomaly Analysis to check for shadows, redundancies, generalizations, correlations and consolidations.Post-Change Policy Analysis—Enables you to clean the existing rulebase by identifying shadows, redundancies, and other anomalies that have accumulated over time. You can also use Policy Analyzer to add or optimize your Security policy rulebase. Before adding a new rule—Check to seeFirewall Policy Analyzer - FireMon.com
Skip to main content Documentation Overview Guides Reference Resources Technology areas Cross-product tools Related sites Console Contact Us Start free Discover Product overview Understand policies and usage Analyze policies Policy Analyzer for allow policiesAnalyze allow policiesAnalyze organization policiesManage saved queriesWrite policy analysis to BigQueryWrite policy analysis to Cloud Storage Improve your policies Prevent policy misconfigurations Test organization policy changes with Policy Simulator Monitor Audit logging for Policy Simulator Stay organized with collections Save and categorize content based on your preferences. This page shows you how to use Activity Analyzer to see when your serviceaccounts and keys were last used to call a Google API. These usages are calledauthentication activities.Recent authentication activity can help you identify the service accounts andservice account keys that you no longer use. We recommend disabling or deletingthese unused service accounts and keys because they create an unnecessarysecurity risk.Before you beginUnderstand authentication activities. Enable the Policy Analyzer API. Enable the API Required roles To get the permissions that you need to list the most recent authentication activities for yourservice accounts and service account keys, ask your administrator to grant you the Activity Analysis Viewer (roles/policyanalyzer.activityAnalysisViewer) IAM role on the project. For more information about granting roles, see Manage access to projects, folders, and organizations. This predefined role contains the permissions required to list the most recent authentication activities for yourservice accounts and service account keys. To see the exact permissions that are required, expand the Required permissions section: Required permissions The following permissions are required to list the most recent authentication activities for yourservice accounts and service account keys: policyanalyzer.serviceAccountKeyLastAuthenticationActivities.query policyanalyzer.serviceAccountLastAuthenticationActivities.query You might also be able to get these permissions with custom roles or other predefined roles. View recent usage for all service accounts or keysTo list the dates of the most recent authentication activities for all. Can Policy Analyzer and Optimizer detect new changes to an already-analyzed policy and run analysis again on the same policy? No, the Policy Analyzer and Optimizer can analyze policies only when manually triggered or at a 24-hour scheduled policy analysis run.Microsoft Policy Analyzer not working
Share via 2022-03-25T08:50:09.173+00:00 I downloaded the PolicyAnalyzer tool to compare some GPOs from different domains in my environment. After following the steps provided, seems after comparing, it does not list everything on the GPO itself. im looking for specific settings only. but its not there. is there something im missing? Thanks! 1 answer 2022-03-31T13:44:12.453+00:00 Hi @Azizan This might occur if there is a non-US language used for setting up the GPO. Below are some recommendations that might as well help you in getting proper results from a policy analyzer. -Add all of the files from GPOs under C:\Windows\SYSVOL\domain\Policies{GPO GUID} on the domain controller. (You could find the group policy name and GUID in the details of GPMC) If there are user configurations in one GPO, check if there have a registry.pol file under C:\Windows\SYSVOL\domain\Policies{GPO GUID}\User when adding policy files in Policy Analyzer. Here is some thread that discusses the same issue and you can try out some troubleshooting steps from this and see if that helps you to sort the Issue. Policy Analyzer not working Hope this resolves your Query!! -- --If the reply is helpful, please Upvote and Accept it as an answer– Sign in to answer Your answer Answers can be marked as Accepted Answers by the question author, which helps users to know the answer solved the author's problem. Question activityComments
EN EnglishDeutschFrançaisEspañolPortuguêsItalianoRomânNederlandsLatinaDanskSvenskaNorskMagyarBahasa IndonesiaTürkçeSuomiLatvianLithuaniančeskýрусскийбългарскиالعربيةUnknown Login to YUMPU News Login to YUMPU Publishing CLOSE TRY ADFREE Discover products News Publishing Magazines Create ePaper Login to YUMPU News Login to YUMPU Publishing 13.07.2015 • Views Share Embed Flag Protocol Analyzer - EventHelix.com Protocol Analyzer - EventHelix.com SHOW MORE SHOW LESS ePAPER READ DOWNLOAD ePAPER TAGS protocol visualether analyzer template filter extraction sequence display destination examples eventhelix.com You also want an ePaper? Increase the reach of your titles YUMPU automatically turns print PDFs into web optimized ePapers that Google loves. START NOW More documents Recommendations Info Page 4: VISUALETHER PROTOCOL ANALYZER 6.1WiPage 9 and 10: VISUALETHER PROTOCOL ANALYZER 6.14 Page 11 and 12: VISUALETHER PROTOCOL ANALYZER 6.12 Page 13: VISUALETHER PROTOCOL ANALYZER 6.1BoPage 16 and 17: VISUALETHER PROTOCOL ANALYZER 6.1SpPage 18: VISUALETHER PROTOCOL ANALYZER 6.1DrPage 21 and 22: VISUALETHER PROTOCOL ANALYZER 6.1ExPage 23 and 24: VISUALETHER PROTOCOL ANALYZER 6.1ruPage 25 and 26: VISUALETHER PROTOCOL ANALYZER 6.1tcPage 27 and 28: VISUALETHER PROTOCOL ANALYZER 6.1SpPage 29 and 30: VISUALETHER PROTOCOL ANALYZER 6.1AtPage 31 and 32: VISUALETHER PROTOCOL ANALYZER 6.1WoPage 33 and 34: VISUALETHER PROTOCOL ANALYZER 6.1SIPage 35 and 36: VISUALETHER PROTOCOL ANALYZER 6.1LI Delete template? Are you sure you want to delete your template? Save as template ? Title Description no error products FREE adFREE WEBKiosk APPKiosk PROKiosk Resources Blog API Help & Support Status tuxbrain.comooomacros.orgnubuntu.org Company Contact us Careers Terms of service Privacy policy Cookie policy Cookie settings Imprint Terms of service Privacy policy Cookie policy Cookie settings Imprint Change language Made with love in Switzerland © 2025 Yumpu.com all rights reserved
2025-04-15Firewall Policy AnalyzerA no-risk, no-cost firewall analyzer to help enhance your security posture. One misconfigured rule is one too many Misconfigurations are a well-documented source of the expanding cybersecurity gap, especially when it comes to an organization’s firewall. With traditional rules-based firewall setups becoming cumbersome to manage manually as environments grow, human errors can quickly add up if not identified and corrected, compromising your entire security infrastructure.FireMon’s firewall Policy Analyzer simplifies the process of identifying and correcting misconfigurations, providing a fast, reliable solution to strengthen your security posture and close cybersecurity gaps. “99% of firewall breaches will be caused by misconfigurations, not firewalls.” Policy Analyzer that Reduces Risk FireMon Policy Analyzer is a complimentary firewall rule analysis solution that provides best practices and suggestions to reduce policy-related risk. Within minutes, our firewall analyzer shares a diagnostic report outlining the security hygiene of a single firewall configuration in your environment, complete with key areas of interest and remediation recommendations. Get a Demo FireMon Policy Analyzer Delivers: Assessment results available in minutes with no installation, setup, or dedicated hardware Key results include overly permissive, risky access, vendor hardening, and policy quality warnings Comprehensive analysis highlights gaps in compliance and security posture, enabling quick remediation and improved policy management Validation to see if changes improve diagnostic scores Downloadable reports to dive deeper into the results and share with others Top remediation recommendations based on FireMon’s 20+ years of experience Get a demo Protect Your Enterprise with Comprehensive Firewall Analyzer Tools Enhance security and compliance with advanced tools to monitor logs, analyze traffic in real time, and review policies—ensuring your firewall stays optimized and secure. Monitor and Analyze Firewall Logs Leverage a firewall log analyzer to gain visibility into network activity, detect threats, and ensure compliance. Track events, identify vulnerabilities, and strengthen security posture.Continuously
2025-04-01Digital assets. Why Are Up-to-Date Firewall Rules Important for Cybersecurity? Up-to-date firewall rules are crucial for cybersecurity because they ensure that only authorized traffic can access your network, effectively blocking malicious activity. As cyber threats evolve, outdated rules can leave vulnerabilities that attackers exploit.Regular updates and analysis of your firewall policies using a policy analyzer can help you adapt to new threats, maintain compliance, and optimize network performance. Without a system in place for analyzing rule sets, your network could become an easy target for cybercriminals, leading to potential data breaches and significant financial and reputational damage. What Benefits Does a Firewall Analyzer Offer? A firewall analyzer offers several benefits, including enhanced security through regular audits and compliance checks, ensuring firewall rules are optimized and up-to-date. It helps identify and rectify configuration errors, reducing the risk of breaches. Using an automated firewall policy analyzer will also provide visibility into network traffic, aiding in troubleshooting and performance optimization. Additionally, it simplifies management by generating reports and alerts, allowing administrators to proactively address potential issues and maintain robust security policies efficiently. Will a Policy Analyzer Reduce the Workload for My Security Team? Yes, a policy analyzer reduces your security team’s workload by automating rule analysis and identifying misconfigurations. Combined with firewall auditing software, it streamlines compliance checks, simplifies reporting, and provides remediation recommendations. This automation minimizes manual effort, enabling teams to focus on strategic initiatives while maintaining a secure and optimized firewall environment. What Types of Threats Are Commonly Detected with a Firewall Policy Analyzer? A firewall policy analyzer detects threats such as overly permissive rules, misconfigurations, unauthorized access attempts, and policy violations. It also identifies vulnerabilities from outdated rules, insecure protocols, and risky access paths. Combined with firewall auditing software, it helps uncover compliance gaps and weak points that attackers could
2025-04-22If new rules need to be added. Policy Analyzer recommends how best to change your existing Security policy rules to meet your requirements without adding another rule, if possible.Streamline and optimize your existing rulebase—See where you can update your rules to minimize bloat and eliminate conflicts and also to ensure that traffic enforcement aligns with the intent of your Security policy rulebase. Test Security Rules (PAN-OS & Panorama) Test the traffic policy matches of the running firewall configuration. Panorama customers with the Cloud Connector Plugin can use Policy Analyzer to analyze Security rules both before and after committing changes to their configuration. Policy Analyzer not only analyzes and provides suggestions for possible consolidation or removal of specific rules to meet your intent but also checks for anomalies, such as Shadows, Redundancies, Generalizations, Correlations and Consolidations in your rulebase. Policy Analyzer requires the Cloud Connector Plugin 1.1.0 on your Panorama appliance.Policy Analyzer requires Panorama to be updated to PAN-OS version 10.2.3 or a later version. Both Panorama and PAN-OS customers can test and verify that security rules are allowing and denying the correct traffic by executing policy match tests for firewalls directly from the web interface. Select to perform a policy match or connectivity test. Enter the required information to perform the policy match test. In this example, we run a NAT policy match test.Select Test—Select NAT Policy Match.From—Select the zone traffic is originating from.To—Select the target zone of the traffic.Source—Enter the IP address from which traffic originated.Destination—Enter the IP address
2025-04-06