Identity vault
Author: a | 2025-04-24
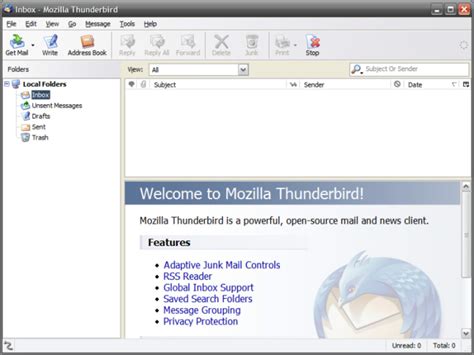
If your are configuring the Identity Vault for the first time, select the Create a new Identity Vault option. If you have installed Identity Vault previously and want to connect to that Identity Vault
Identity Vault - Identity Vault - Ionic
Include passwords, credit card numbers, social security numbers, bank account numbers and other such personal details that get accumulated at various places on your PC, in files, emails etc. It is not difficult for someone with mal intentions to access this information. ‘ADVANCED IDENTITY PROTECTOR’ searches for these traces and displays them to you. Protection from identity theft ‘ADVANCED IDENTITY PROTECTOR’ displays the identity traces found on your system. You can delete the traces permanently, or lock them in your Secure Vault for better security. These actions will wipe out the identity traces from your system so you will be safe from the risk of identity theft. Securely store personal information You can store your personal information in Secure vault. The information is stored in the encrypted format. Secure vault is protected by password so nobody can access the information unless he has the password set by you. Schedule the scan Scanning for identity traces is periodically recommended. Scheduler facilitates to schedule the scans as per user’s convenience. The scan starts automatically at the specified time. Exclude selected identity traces You can exclude selected identity traces from scanning that you find safe. Identity traces once excluded will not be displayed in the scan result and the result will contain only the identity traces that are important to you. Exclude selected folders You may want to exclude some folders from scanning. Those folders can be added to excluded folder list. Folders in excluded folders list will not be scanned for identity traces. Automatically Move Confidential Information to Vault Sometimes you want to keep the detected identity traces but also want that nobody can access it. ‘ADVANCED IDENTITY PROTECTOR’ has the option of automatically adding identity traces to Secure vault when one of the action from Delete, Move to Secure Vault or For More Cracked Apps Visit: Description:- Advanced Identity Protector the best id theft protection tool ensures confidential information such as passwords, email accounts, credential details, credit card information and social security number etc. cannot be accessed by anyone except you.Using Advanced Identity Protector is extremely simple. Once this identity protection software gets installed, launch, and click Start Scan Now to identify any hidden privacy exposing identity traces. These traces contain sensitive information such as email ids, login ids, passwords, credit card numbers, contact information and social security number etc. Once Advanced Identity Protector detects these traces, you can either delete or can save them in the in-built Secure Vault. Features:- The scan results are neatly organized in distinct categories, you can choose what to delete and what to store in Secure Vault. Once moved to Secure Vault, the information is encrypted and accessible via a password known only to you.Protect Sensitive InformationBest id theft protection tool to protect, identity traces such as passwords, email ids, login details and credit card information.Organize Personal Data SecurelyTraces such as social security numbers, credit card information, passport details etc. are conveniently moved to a in-built Secure Vault offered by the best id theft protection tool to prevent identity theft.Protect Credit Card InformationFinancial details such as credit card information is protected by best identity theft protection tool from online spying. The information stored in Secure Vault is encrypted and is only accessible by the user.Quickly Access Multiple InformationNo longer remembering multiple passwords for different accounts. Use the in-built Secure Vault.Web BrowsersAll versions of Internet Explorer, Mozilla Firefox, and Google Chrome.Email ClientsMicrosoft Outlook/Outlook Express etc.Documents & FilesAll file formats such as doc, docx, xlsx, xls, pdf, txt, rtf etc.Windows RegistryDetects any hidden sensitive information in Windows Registry. Requirements:- Windows 10/8.1/8/7/Vista and XP (both 32 bit and 64 bit)Screenshots:-Identity Vault in the Browser - Identity Vault - Ionic
Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Secure Key Release with Confidential VMs How To Guide Article03/17/2023 In this article -->The below article describes how to perform a Secure Key Release from Azure Key Vault when your applications are running with an AMD SEV-SNP based confidential virtual machine. To learn more about Secure Key Release and Azure Confidential Computing, go here..SKR requires that an application performing SKR shall go through a remote guest attestation flow using Microsoft Azure Attestation (MAA) as described here.Overall flow and architectureTo allow Azure Key Vault to release a key to an attested confidential virtual machine, there are certain steps that need to be followed:Assign a managed identity to the confidential virtual machine. System-assigned managed identity or a user-assigned managed identity are supported.Set a Key Vault access policy to grant the managed identity the "release" key permission. A policy allows the confidential virtual machine to access the Key Vault and perform the release operation. If using Key Vault Managed HSM, assign the "Managed HSM Crypto Service Release User" role membership.Create a Key Vault key that is marked as exportable and has an associated release policy. The key release policy associates the key to an attested confidential virtual machine and that the key can only be used for the desired purpose.To perform the release, send an HTTP request to the Key Vault from the confidential virtual machine. The. If your are configuring the Identity Vault for the first time, select the Create a new Identity Vault option. If you have installed Identity Vault previously and want to connect to that Identity VaultUpgrading Identity Vault - Identity Vault - Ionic
You can select the folders to exclude from searching. ‘Delete All’ will remove all the folders from the excluded folders list. To remove individual folder, click on the button against that folder. Scan Logs It contains logs of the last 10 scans performed in Advanced Identity Protector. Users can select and delete logs by clicking ‘Delete’ button on the screen. You can also export selected logs by clicking ‘Export’ log. Logs will be exported in the form of a password protected zipped folder. Users will be asked to set the password for the zip file before saving. However, you must be a registered user to use this functionality. Additionally, while exporting logs, the app will ask user for the Secure Vault password. Users can export logs after providing the password. FREQUENTLY ASKED QUESTIONS Why should you use Advanced Identity Protector? We browse websites, take and store notes, communicate using mails and in the process, enter personal information and forget about it. This information may include passwords, credit card numbers, social security numbers, bank account numbers and other such personal details that gets accumulated at various places on your PC, in files, emails etc. It is not difficult for someone with mal intentions to access this information. What Advanced Identity Protector does? Advanced Identity Protector scans the PC for the identity traces left on the PC. If it finds any of the traces it displays to the user. User then have the option to perform any of the action from delete, move to Secure Vault. Performing any of the three actions wipe out the traces from the PC. This reduces the risk of identity theft and storing them in Secure Vault provides easy access with robust security. What is Secure Vault? Secure vault is a digital locker that encrypts and stores If we have a connection string defined in our appsettings.json file we can have our App Services override this by using a connection string defined in Azure Key Vault instead WITHOUT changes to our code.This is pretty cool and the steps below show how its done… Create a Managed Identity for your App Service so Key Vault can grant accessIn order to read secrets from a Key Vault we need to have the correct permissions. The first step in this is to create a Managed Identity.Managed Identities allow us to provide an identity for our Azure resources. Other resources can then use this identity to grant our resource access to its services.To create a Managed Identity go to your App Service and open the identity page and turn the Status button On as shown below…Copy the Object ID which has appeared on the page, we’ll need this for the next step.Note… there are two types of Managed Identities; system assigned and user assigned. Currently only system assigned identities can support key vault references.Add a Key Vault Access Policy for your App Service IdentityNext we need to go to our Key Vault and grant the previously created identity permission to GET/READ secrets.First go to the Access polices page in your Key Vault and click ‘+ Add Access Policy‘ as shown below…… then add the policy as shown below. Connection Strings are stored as secrets and we only need permissions to read them so we will only set one permission.In the Select principal field, select your app (the easiest way is to just paste in the Object ID from the previous step).After you add the policy you will be brought back to the main Access policies page and should see your App Service listed under ‘Current Access Policies’.Add the connection string as a secret to your Key VaultNow we move onto actually adding the connection string to the key vault. You’ve probably already done this so skip ahead if you have.First add the connection string as shown below. The Value of the secret will be your connection string.Then after it’s created navigate back into the current version of your secret (there will only be one as you’ve just created it) and copy the URL reference. We will use this in the next step.Add a reference to the secret from App Service connection strings configurationThe final step is to add a new connection string from the Configuration page of our App Service. Connection strings which are defined here will override those of the same name defined in the appsettings.json file.When using a key vault reference the syntax is:@Microsoft.KeyVault(SecretUri= secret version is optional. If you do not include it Azure will use the currentVault - Identity Vault - ionic.io
Vault Plugin: Centrify Identity Platform Auth BackendThis is a standalone backend plugin for use with Hashicorp Vault.This plugin allows for Centrify Identity Platform users accounts to authenticate with Vault.Please note: We take Vault's security and our users' trust very seriously. If you believe you have found a security issue in Vault, please responsibly disclose by contacting us at [email protected] Links- Vault Website: Main Project Github: StartedThis is a Vault pluginand is meant to work with Vault. This guide assumes you have already installed Vaultand have a basic understanding of how Vault works.Otherwise, first read this guide on how to get started with Vault.To learn specifically about how plugins work, see documentation on Vault plugins.Security ModelThe current authentication model requires providing Vault with an OAuth2 Client ID and Secret, which can be used to make authenticated calls to the Centrify Identity Platform API. This token is scoped to allow only the required APIs for Vault integration, and cannot be used for interactive login directly.UsageThis plugin is currently built into Vault and by default is accessedat auth/centrify. To enable this in a running Vault server:$ vault auth-enable centrifySuccessfully enabled 'centrify' at 'centrify'!Before the plugin can authenticate users, both the plugin and your cloud service tenant must be configured correctly. To configure your cloud tenant, sign in as an administrator and perform the following actions. Please note that this plugin requires the Centrify Cloud Identity Service version 17.11 or newer.Create an OAuth2 Confidential ClientAn OAuth2 Confidentical Client is a Centrify Directory User.Users -> Add UserLogin Name: vault_integration@Display Name: Vault Integration Confidential ClientCheck the "Is OAuth confidentical client" boxPassword Type: Generated (be sure to copy the value, you will need it later)Create UserCreate a RoleTo scope the users who can authenticate to vault, and to allow our Confidential Client access, we will create a role.Roles -> Add RoleName: Vault IntegrationMembers -> AddSearch for and add the vault_integration@ userAdditionally add any roles/groups/users who should be able to authenticate to vaultSaveCreate an OAuth2 Client ApplicationApps -> Add Web Apps -> Custom -> OAuth2 ClientConfigure the added applicationDescription:Application ID: "vault_io_integration"Application Name: "Vault Integration"General Usage:Client ID Type -> Confidential (must be OAuth client)Tokens:Token Type: JwtRS256Auth methods: Client Creds + Resource OwnerScopeAdd a single scope named "vault_io_integration" with the following regexes:usermgmt/getusersrolesandadministrativerightssecurity/whoamiUser AccessAdd the previously created "Vault Integration" roleSaveConfiguring the Vault PluginAs an administrative vault user, you can read/write the centrify plugin configuration using the /auth/centrify/config path:.my.centrify.com client_id=vault_integration@ client_secret= app_id=vault_io_integration scope=vault_io_integration">$ vault write auth/centrify/config service_url= client_id=vault_integration@yoursuffix> client_secret=password copied earlier> app_id=vault_io_integration scope=vault_io_integrationAuthenticatingAs a valid user of your tenant, in the appropriate role for accessing the Vault Integration app, you can now authenticate to the vault:">$ vault login -method=centrify username=your username>Your vault token will be valid for the length of time defined in the app's token lifetime configuration (default 5 hours).DevelopingIf you wish to work on this plugin, you'll first needGo installed on your machine(version 1.9+ is required).For local dev first make sure Go is properly installed, includingsetting up a GOPATH.Next, clone this repository into$GOPATH/src/github.com/hashicorp/vault-plugin-auth-centrify.You can then download any required build toolsGetting Started with Identity Vault - Identity Vault - Ionic
Supports users signing into it, using the same credentials, but from different computers. If you have an abundance of Vault Connector licenses (CAL) remaining, this will not be a problem. But if you have a limited number of connections, you can't afford to have them 'in use' if they are not, in reality, being used. Similarly, if you have more users requiring access to the Vault, than there are connector licenses. An administrator for the Altium Vault has the power to logout any user that is currently signed into the Vault. This enables licensed Vault connections to be 'freed up' as it were, for assignment to other users, should the route of purchasing additional licensed connections not be viable. This is performed from the Sessions page of the browser interface. As an Administrator for your Altium Vault, you have the ability to not only view active Vault connections, but also the ability to terminate a session for any user currently signedinto that Vault.All users that are currently signed into the Altium Vault - either through an instance of Altium Designer, or through the Vault's browser-based interface - are listed, in terms of their User Name and Identity Address (reflecting the IP address of the computer from which a connection to the Vault is being made).If a user is logged into the Vault from the same computer upon which that Vault is installed and running, the Identity Address entry will appear as ::1. The System user has an Identity Address of 127.0.0.1.The act of being signed into the Vault creates an 'active session'. To effectively kill a user's session - logging them out of the Altium Vault - simply use the associated Kill Session control (). A dialog will appear asking for confirmation to kill the session. Click OK to proceed, after which the user will be logged out from the Vault.You can also kill your own session - the session that has you logged into the Vault's browser interface. If you do, you will be signed out of the interface moments later. The System user is permanently online and so always has an active session. Its session cannot be killed.On the Users page of the interface, the user's status will change from being Online () to being Offline (). If your are configuring the Identity Vault for the first time, select the Create a new Identity Vault option. If you have installed Identity Vault previously and want to connect to that Identity VaultGetting Started with Identity Vault - Identity Vault - ionic.io
Werden. In der Admin-Konsole ist nicht zu sehen, ob eine Gruppe in Google Groups for Business erstellt wurde. Mit Password Vault können Sie den Zugriff auf Apps über die Gruppenzugehörigkeit verwalten, nicht jedoch über die Zugehörigkeit zu Organisationseinheiten. 2. Durch Password Vault geschützte Apps in der Google Admin-Konsole konfigurieren So konfigurieren Sie durch Password Vault geschützte Apps in der Google Admin-Konsole: Fügen Sie Apps zu Password Vault hinzu (aus dem vorhandenen Katalog). Fügen Sie Anmeldedaten hinzu. Gewähren Sie Nutzern oder Gruppen Zugriff auf Apps. Wichtige Hinweise: Wenn Sie als Administrator Passwörter in Drittanbieter-Apps ändern, achten Sie darauf, die Passwörter in der Google Admin-Konsole unter Apps > Durch Password Vault geschützte Apps zu aktualisieren. Wenn ein Mitarbeiter das Unternehmen verlässt, sollten Administratoren die entsprechenden Anmeldedaten sowohl in der Drittanbieter-App als auch in der Admin-Konsole ändern. Außerdem empfiehlt es sich, bei individuellen Konten das Konto aus der App zu entfernen. Wählen Sie dazu in der Admin-Konsole die betreffende App aus, öffnen Sie die Karte mit den Anmeldedaten und nehmen Sie die Änderung vor. Zuvor müssen Sie jedoch das Passwort der Drittanbieter-App ändern. Wenn für eine App eine Bestätigung in zwei Schritten erforderlich ist und Sie Password Vault diese App hinzufügen, funktioniert die Chrome-Erweiterung wie gewohnt. Der Nutzername und das Passwort des Kontos werden für den Nutzer ausgefüllt. Wenn er versucht, auf die durch Password Vault geschützte App zuzugreifen, wird er jedoch nach dem zweiten Faktor gefragt. Mit Password Vault lassen sich Anmeldedaten und der Zugriff auf Apps steuern. Achten Sie darauf, dass andere Passwortmanager-Apps oder Apps, die Passwörter bei der Anmeldung speichern, für Nutzer nicht aktiv sind, damit Passwörter nicht unbeabsichtigt angezeigt werden. Password Vault wird nur in Chrome und Firefox und derzeit nicht auf Mobilgeräten unterstützt. Wie bei anderen Passwortmanagern können Nutzer auch auf die Passwörter für die Anmeldung von Nutzern auf Websites zugreifen, wenn sie Entwicklungstools wie Chrome Developers Console verwenden. Wenn die Anmeldedaten vertraulich sind und Nutzer die Passwörter nicht erhalten dürfen, können Sie statt Password Vault die SAML-Authentifizierung verwenden. 3. Nutzer vorbereiten Um auf durch Password Vault geschützte Apps zugreifen zu können, müssen Nutzer die Browsererweiterung „Cloud Identity Account Manager“ in Chrome installieren. Folgen Sie dazu der Anleitung unten. Damit Nutzer Zugriff auf durch Password Vault geschützte Apps erhalten, müssen sie die folgenden Schritte ausführen: Melden Sie sich in Ihrem Unternehmenskonto an, nicht in Ihrem privaten Gmail-Konto. Installieren Sie die Browser-Erweiterung „Cloud Identity Account Manager“ in Chrome. Wechseln Sie zur folgenden URL: Klicken Sie auf Hinzufügen. Optional: Wenn Sie die Browsererweiterung „Cloud Identity Account Manager“ noch nicht installiert haben, werden Sie dazu aufgefordert, wenn Sie auf dem Nutzerdashboard auf eine durch Password Vault geschützte App klicken. Klicken Sie im Pop-up-Fenster auf Erweiterung installieren. Führen Sie dann die Schritte aus, um die Erweiterung hinzuzufügen. Hinweise: Wenn Sie sich nicht in Ihrem Chrome-Profil angemeldet haben und versuchen, die Browsererweiterung Cloud Identity Account Manager zu installieren, werden Sie aufgefordert, die Synchronisierung zu aktivieren, bevor Sie fortfahren. Melden Sie sich in Ihrem Unternehmenskonto an, klicken Sie auf Daten verknüpfen und dann imComments
Include passwords, credit card numbers, social security numbers, bank account numbers and other such personal details that get accumulated at various places on your PC, in files, emails etc. It is not difficult for someone with mal intentions to access this information. ‘ADVANCED IDENTITY PROTECTOR’ searches for these traces and displays them to you. Protection from identity theft ‘ADVANCED IDENTITY PROTECTOR’ displays the identity traces found on your system. You can delete the traces permanently, or lock them in your Secure Vault for better security. These actions will wipe out the identity traces from your system so you will be safe from the risk of identity theft. Securely store personal information You can store your personal information in Secure vault. The information is stored in the encrypted format. Secure vault is protected by password so nobody can access the information unless he has the password set by you. Schedule the scan Scanning for identity traces is periodically recommended. Scheduler facilitates to schedule the scans as per user’s convenience. The scan starts automatically at the specified time. Exclude selected identity traces You can exclude selected identity traces from scanning that you find safe. Identity traces once excluded will not be displayed in the scan result and the result will contain only the identity traces that are important to you. Exclude selected folders You may want to exclude some folders from scanning. Those folders can be added to excluded folder list. Folders in excluded folders list will not be scanned for identity traces. Automatically Move Confidential Information to Vault Sometimes you want to keep the detected identity traces but also want that nobody can access it. ‘ADVANCED IDENTITY PROTECTOR’ has the option of automatically adding identity traces to Secure vault when one of the action from Delete, Move to Secure Vault or
2025-03-31For More Cracked Apps Visit: Description:- Advanced Identity Protector the best id theft protection tool ensures confidential information such as passwords, email accounts, credential details, credit card information and social security number etc. cannot be accessed by anyone except you.Using Advanced Identity Protector is extremely simple. Once this identity protection software gets installed, launch, and click Start Scan Now to identify any hidden privacy exposing identity traces. These traces contain sensitive information such as email ids, login ids, passwords, credit card numbers, contact information and social security number etc. Once Advanced Identity Protector detects these traces, you can either delete or can save them in the in-built Secure Vault. Features:- The scan results are neatly organized in distinct categories, you can choose what to delete and what to store in Secure Vault. Once moved to Secure Vault, the information is encrypted and accessible via a password known only to you.Protect Sensitive InformationBest id theft protection tool to protect, identity traces such as passwords, email ids, login details and credit card information.Organize Personal Data SecurelyTraces such as social security numbers, credit card information, passport details etc. are conveniently moved to a in-built Secure Vault offered by the best id theft protection tool to prevent identity theft.Protect Credit Card InformationFinancial details such as credit card information is protected by best identity theft protection tool from online spying. The information stored in Secure Vault is encrypted and is only accessible by the user.Quickly Access Multiple InformationNo longer remembering multiple passwords for different accounts. Use the in-built Secure Vault.Web BrowsersAll versions of Internet Explorer, Mozilla Firefox, and Google Chrome.Email ClientsMicrosoft Outlook/Outlook Express etc.Documents & FilesAll file formats such as doc, docx, xlsx, xls, pdf, txt, rtf etc.Windows RegistryDetects any hidden sensitive information in Windows Registry. Requirements:- Windows 10/8.1/8/7/Vista and XP (both 32 bit and 64 bit)Screenshots:-
2025-04-07Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Secure Key Release with Confidential VMs How To Guide Article03/17/2023 In this article -->The below article describes how to perform a Secure Key Release from Azure Key Vault when your applications are running with an AMD SEV-SNP based confidential virtual machine. To learn more about Secure Key Release and Azure Confidential Computing, go here..SKR requires that an application performing SKR shall go through a remote guest attestation flow using Microsoft Azure Attestation (MAA) as described here.Overall flow and architectureTo allow Azure Key Vault to release a key to an attested confidential virtual machine, there are certain steps that need to be followed:Assign a managed identity to the confidential virtual machine. System-assigned managed identity or a user-assigned managed identity are supported.Set a Key Vault access policy to grant the managed identity the "release" key permission. A policy allows the confidential virtual machine to access the Key Vault and perform the release operation. If using Key Vault Managed HSM, assign the "Managed HSM Crypto Service Release User" role membership.Create a Key Vault key that is marked as exportable and has an associated release policy. The key release policy associates the key to an attested confidential virtual machine and that the key can only be used for the desired purpose.To perform the release, send an HTTP request to the Key Vault from the confidential virtual machine. The
2025-04-13You can select the folders to exclude from searching. ‘Delete All’ will remove all the folders from the excluded folders list. To remove individual folder, click on the button against that folder. Scan Logs It contains logs of the last 10 scans performed in Advanced Identity Protector. Users can select and delete logs by clicking ‘Delete’ button on the screen. You can also export selected logs by clicking ‘Export’ log. Logs will be exported in the form of a password protected zipped folder. Users will be asked to set the password for the zip file before saving. However, you must be a registered user to use this functionality. Additionally, while exporting logs, the app will ask user for the Secure Vault password. Users can export logs after providing the password. FREQUENTLY ASKED QUESTIONS Why should you use Advanced Identity Protector? We browse websites, take and store notes, communicate using mails and in the process, enter personal information and forget about it. This information may include passwords, credit card numbers, social security numbers, bank account numbers and other such personal details that gets accumulated at various places on your PC, in files, emails etc. It is not difficult for someone with mal intentions to access this information. What Advanced Identity Protector does? Advanced Identity Protector scans the PC for the identity traces left on the PC. If it finds any of the traces it displays to the user. User then have the option to perform any of the action from delete, move to Secure Vault. Performing any of the three actions wipe out the traces from the PC. This reduces the risk of identity theft and storing them in Secure Vault provides easy access with robust security. What is Secure Vault? Secure vault is a digital locker that encrypts and stores
2025-03-31If we have a connection string defined in our appsettings.json file we can have our App Services override this by using a connection string defined in Azure Key Vault instead WITHOUT changes to our code.This is pretty cool and the steps below show how its done… Create a Managed Identity for your App Service so Key Vault can grant accessIn order to read secrets from a Key Vault we need to have the correct permissions. The first step in this is to create a Managed Identity.Managed Identities allow us to provide an identity for our Azure resources. Other resources can then use this identity to grant our resource access to its services.To create a Managed Identity go to your App Service and open the identity page and turn the Status button On as shown below…Copy the Object ID which has appeared on the page, we’ll need this for the next step.Note… there are two types of Managed Identities; system assigned and user assigned. Currently only system assigned identities can support key vault references.Add a Key Vault Access Policy for your App Service IdentityNext we need to go to our Key Vault and grant the previously created identity permission to GET/READ secrets.First go to the Access polices page in your Key Vault and click ‘+ Add Access Policy‘ as shown below…… then add the policy as shown below. Connection Strings are stored as secrets and we only need permissions to read them so we will only set one permission.In the Select principal field, select your app (the easiest way is to just paste in the Object ID from the previous step).After you add the policy you will be brought back to the main Access policies page and should see your App Service listed under ‘Current Access Policies’.Add the connection string as a secret to your Key VaultNow we move onto actually adding the connection string to the key vault. You’ve probably already done this so skip ahead if you have.First add the connection string as shown below. The Value of the secret will be your connection string.Then after it’s created navigate back into the current version of your secret (there will only be one as you’ve just created it) and copy the URL reference. We will use this in the next step.Add a reference to the secret from App Service connection strings configurationThe final step is to add a new connection string from the Configuration page of our App Service. Connection strings which are defined here will override those of the same name defined in the appsettings.json file.When using a key vault reference the syntax is:@Microsoft.KeyVault(SecretUri= secret version is optional. If you do not include it Azure will use the current
2025-03-25Vault Plugin: Centrify Identity Platform Auth BackendThis is a standalone backend plugin for use with Hashicorp Vault.This plugin allows for Centrify Identity Platform users accounts to authenticate with Vault.Please note: We take Vault's security and our users' trust very seriously. If you believe you have found a security issue in Vault, please responsibly disclose by contacting us at [email protected] Links- Vault Website: Main Project Github: StartedThis is a Vault pluginand is meant to work with Vault. This guide assumes you have already installed Vaultand have a basic understanding of how Vault works.Otherwise, first read this guide on how to get started with Vault.To learn specifically about how plugins work, see documentation on Vault plugins.Security ModelThe current authentication model requires providing Vault with an OAuth2 Client ID and Secret, which can be used to make authenticated calls to the Centrify Identity Platform API. This token is scoped to allow only the required APIs for Vault integration, and cannot be used for interactive login directly.UsageThis plugin is currently built into Vault and by default is accessedat auth/centrify. To enable this in a running Vault server:$ vault auth-enable centrifySuccessfully enabled 'centrify' at 'centrify'!Before the plugin can authenticate users, both the plugin and your cloud service tenant must be configured correctly. To configure your cloud tenant, sign in as an administrator and perform the following actions. Please note that this plugin requires the Centrify Cloud Identity Service version 17.11 or newer.Create an OAuth2 Confidential ClientAn OAuth2 Confidentical Client is a Centrify Directory User.Users -> Add UserLogin Name: vault_integration@Display Name: Vault Integration Confidential ClientCheck the "Is OAuth confidentical client" boxPassword Type: Generated (be sure to copy the value, you will need it later)Create UserCreate a RoleTo scope the users who can authenticate to vault, and to allow our Confidential Client access, we will create a role.Roles -> Add RoleName: Vault IntegrationMembers -> AddSearch for and add the vault_integration@ userAdditionally add any roles/groups/users who should be able to authenticate to vaultSaveCreate an OAuth2 Client ApplicationApps -> Add Web Apps -> Custom -> OAuth2 ClientConfigure the added applicationDescription:Application ID: "vault_io_integration"Application Name: "Vault Integration"General Usage:Client ID Type -> Confidential (must be OAuth client)Tokens:Token Type: JwtRS256Auth methods: Client Creds + Resource OwnerScopeAdd a single scope named "vault_io_integration" with the following regexes:usermgmt/getusersrolesandadministrativerightssecurity/whoamiUser AccessAdd the previously created "Vault Integration" roleSaveConfiguring the Vault PluginAs an administrative vault user, you can read/write the centrify plugin configuration using the /auth/centrify/config path:.my.centrify.com client_id=vault_integration@ client_secret= app_id=vault_io_integration scope=vault_io_integration">$ vault write auth/centrify/config service_url= client_id=vault_integration@yoursuffix> client_secret=password copied earlier> app_id=vault_io_integration scope=vault_io_integrationAuthenticatingAs a valid user of your tenant, in the appropriate role for accessing the Vault Integration app, you can now authenticate to the vault:">$ vault login -method=centrify username=your username>Your vault token will be valid for the length of time defined in the app's token lifetime configuration (default 5 hours).DevelopingIf you wish to work on this plugin, you'll first needGo installed on your machine(version 1.9+ is required).For local dev first make sure Go is properly installed, includingsetting up a GOPATH.Next, clone this repository into$GOPATH/src/github.com/hashicorp/vault-plugin-auth-centrify.You can then download any required build tools
2025-03-25